Saturday, April 18, 2009
Funny Trick In Windows XP
Create Cmd Prompt When Your Command Prompt Does Not Work
Fun With Browser

Funny Computer Tricks: Check out these tips and funny tricks
(1)Fun With Browser :
Copy and paste the java script code in the following red lines to the address bar of your browser
javascript:function Shw(n) {if (self.moveBy) {for (i = 35; i > 0; i--) {for (j = n; j > 0; j--) {self.moveBy(1,i);self.moveBy(i,0);self.moveBy(0,-i);self.moveBy(-i,0); } } }} Shw(6)
Press enter and watch your window's |shaking it" You can change the value of i if you wish :-)
Phishing the Phisher : A Counter Attack Tutorial

This post will explain you about Phishing which came across me when I used to learn hacking related stuffs. In this post I will be explaining you mode of operation of Phishing starting from scratch. Though phishing is old ,it poses as a great threat in the world wild wide web. For security it is needed to get into the source loop holes. So, lets start without wasting much time.
Definition
Phishing is simply the act of creating fake page of any legitimate web-service and host them on net in order to fool the user to get the passwords, credit card no .,social security no. etc
Requirements
1. Web browser (mozilla firefox, internet explorer)
2. Text editor (ex: notepad ,kwrite)
3. Knowledge of basic HTML and some scripting languages like php, javascript etc.
4. Web hosting resource
Mode of operation::
I will provide quite simple steps.
1.The source code of the target website is obtained by using in built function of web browsers .
Ex: For mozilla firefox page source code can be obtained by
option 1) by navigating to page source present in edit tab.
option 2) pressing ctrl+u
option 3) right clicking and selecting view page source
2. All the source code is copied into an editor.
3. Now , the action attribute of form element is searched.
• Form elements are elements that allow the user to enter information (like text fields of username ,password , textarea fields, drop-down menus, radio buttons, checkboxes, etc.) in a form.
•When the user clicks on the "Submit" button, the content of the form is sent to the server. The form's action attribute defines the name of the file to send the content to. The file defined in the action attribute usually does something with the received input.
5. From the above explanation it is quite clear that by editing the action attribute we can send information (like user account information) .
6. As the last step ,manipulated web page is hosted in the web and victims are made to use them using some social engineering technique.
social engineering ::Social engineering is a collection of techniques used to motivate people into performing actions that will reveal confidential information.
Prevention
1. Don't blindly believe any kind of mail without authenticity.
2. While logging in give a close look at the domain name
3. Change your passwords regularly.
4. Use some web-site advisory software (now a days comes with internet security softwares).ex:Wot
5. Always be alert.
Registry Hack to Disable Writing to USB Drives

A common security concern at organizations is allowing users to plug in a usb flash drive, because they could so easily copy corporate data.
Since Windows XP SP2, you can disable writing to USB devices altogether using a simple registry hack.
Here it is:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\StorageDevicePolicies]
“WriteProtect”=dword:00000001
Windows 7 Beta ISO Leaked on torrent trackers
Apparently you won't have to wait until January to get your hands on the Windows 7 Beta release.That's right, there's already been an ISO file leaked to several torrent trackers.
The ISO appears to contain the Windows 7 M1 build (7000) . So far the new build seems to perform slightly better than 6801, and memory usage has been improved. A number of previously hidden features - like the iconized task bar - are also now active.
Before you start asking why there's no link to the file, it's because this is something that we're not supposed to have yet. If you want to get your hands on it, check your favorite torrent search site. Also keep in mind that this is a leak, and there's always the possibility that the ISO has been tampered with.
Create a Backup of Your Blog in Seconds!

If you are regular blogger and want to make a backup of all your precious Blog Database, Now you can do that very easily without much pain. Now, blog backup service is offered by Blogger in Draft. To make a backup of your blog just log in at Blogger.com and go to Settings of your blog, you will find three options under “Blog Tools” Import Blog, Export Blog, Delete Blog.
To save a backup of your blog just “Export Blog” and save that file on your hard disk. You will get an XML file for your backup. This can be very useful if you want to make a backup or if you want to transfer your blog to some other blogging Platform like Word Press.
Put Your Web Page On Desktop

HERE IS A TRICK TO PUT ur web PAGE ON OUR DESKTOP
To put a Web page on your desktop, start by right-clicking on an empty space on the desktop. THEN
Click on "Properties" to open the display properties dialog box.
To add a Web page to ur desktop:
1. Click on the desktop tab in the display properties dialog box
2. Click the "Customize Desktop." button
In the desktop items dialog box, click on the Web tab
The settings on the Web tab allow you to add new Web pages to ur desktop & customize their settings.From this screen, u can add a Web page to your desktop and customize its settings.
How To Read/Open Data From .nbu Files

.nbu files are the backup files created when you create the backup for your Nokia Mobile. It is created using Nokia PC suite and later can be restored to your phone. Only problem is we can’t open the .nbu files without any nokia device.
To overcome this problem we have one software called NOKI. From their site:
Noki is a utility to explore and extract Phone book, SMS, Calendar, Memo, Bookmark and other user files from the backup file of Nokia phone (using Nokia PC Suite).
Features:
* Supports .nbu, .nfb and .nfc.
* contacts.cdb: Symbian Contacts Database for all Symbian phones (include Nokia, Siemens, Sony Ericsson etc.).
* backup.arc: mass storage/SD card backup file.
* Softpedia security certified.
Download
How To View Hidden Files And Folders In Windows 7
Disable Windows Genuine Advantage Notification in 3 Simple Steps

Following three simple steps now you can get rid of Windows Genuine Advantage (WGA) notifications:
1. Reboot Windows in safe mode (hold the f8 key while booting and you will get the option to boot in safe mode) and then:
2. Open Registry Editor (regedit.exe) and search for wgalogon folder and delete it. You should backup up the registry beforehand, in case somethiong goes wrong.
3. In your windows directory search for files wga* and delete them.
You are done!
Now reboot back normally and continue your work. Windows Genuine Advantage will not bother you anymore.
Warning: Use at your own risk. Backup everything before you do.
Adobe Is Spying On Its Users

Dan Moren of Uneasy Silence first posted about the apparent data sniffing on Wednesday night. Using a program for Mac OS called Little Snitch, he was able to discover Adobe's hidden practice.
The data transmission was discovered in Adobe InDesign CS3 for Mac.In any case, at first glance the address may look like a IP address, and a local one if that. In many routers, 192.168.xxx.xxx is used for internal networking. However this address looks different.Data is sent to 192.168.112.2O7.net.
Two things would appear immediately awry to the experienced eye: first, no IP address includes any alphabetic characters in it, this address includes the letter 'O' in place of a zero. Second, it ends in '.net,' and no IP address ends in any kind of DNS suffix.
So where does this data apparently go? Loading up the address itself in a web browser takes the surfer to a page owned by Ominture, a large web analytics company."Yes, Adobe is watching how many times you open your programs. Adobe is spying on users application habits," Moren wrote.
Apparently, Adobe has already addressed this through an article on its Devnet site. It says it uses Omniture to track usage of an application to 'create better user experiences.'
Everyone knows that adobe flash is spyware,google toolbar is spyware, free firewalls and antivirals are spywares too. I see we're back on the privacy kick once again. If you're connected to the net you don't have any privacy. If you think you do, you're exceedingly naive. Slashdot had an article about cable and DSL suppliers monitoring their customers use of bit torrent for file sharing and shutting down those who do. That means you are being watched. If that scares you, you need to stop using your computer. There are way too many people on the net anyway.
Cool DOS Commands

Command #1: By typing in 'tree' into Dos, you can view all of the folders (not files) on the computer or User. Pretty cool but then again pretty worthless. Just a cool thing to know.
Command #2: By typing in 'ipconfig' you can view your default gateway ip adress for your router. This is really only useful if you are good with the computer and are trying to fix your internet connection, you can look at what's wrong.
Command #3: By typing in 'format c:' you can delete all the information on your hard drive, if you want to start new or something, but dont do that just to be an idiot.
Command #4: By typing in 'netstat' or 'nbtstat' (both similar) you can view the TCP/IP
Wednesday, April 1, 2009
Learn about search engines
Search engines match queries against an index that they create. The index consists of the words in each document, plus pointers to their locations within the documents. This is called an inverted file. A search engine or IR system comprises four essential modules:
* A document processor
* A query processor
* A search and matching function
* A ranking capability
While users focus on “search,” the search and matching function is only one of the four modules. Each of these four modules may cause the expected or unexpected results that consumers get when they use a search engine.
Read detailed abt this on - www.infotoday.com/searcher/may01/liddy.htm
The term “search engine” is often used generically to describe both crawler-based search engines and human-powered directories. These two types of search engines gather their listings in radically different ways.
Crawler-based search engines, such as Google, create their listings automatically. They “crawl” or “spider” the web, then people search through what they have found.
If you change your web pages, crawler-based search engines eventually find these changes, and that can affect how you are listed. Page titles, body copy and other elements all play a role.
A man-powered directory, such as the Open Directory, depends on humans for its listings.
You submit a short description to the directory for your entire site, or editors write one for sites they review. A search looks for matches only in the descriptions submitted.
Changing your web pages has no effect on your listing. Things that are useful for improving a listing with a search engine have nothing to do with improving a listing in a directory.
The only exception is that a good site, with good content, might be more likely to get reviewed for free than a poor site.
“Hybrid Search Engines” Or Mixed Results
In the web’s early days, it used to be that a search engine either presented crawler-based results or human-powered listings. Today, it extremely common for both types of results to be presented. Usually, a hybrid search engine will favor one type of listings over another.
For example, MSN Search is more likely to present human-powered listings from LookSmart.
However, it does also present crawler-based results (as provided by Inktomi), especially for more obscure queries.
The Parts Of A Crawler-Based Search Engine
Crawler-based search engines have three major elements. First is the spider, also called the crawler. The spider visits a web page, reads it, and then follows links to other pages within the site. This is what it means when someone refers to a site being “spidered” or “crawled.” The spider returns to the site on a regular basis, such as every month or two, to look for changes.
Everything the spider finds goes into the second part of the search engine, the index. The index, sometimes called the catalog, is like a giant book containing a copy of every web page that the spider finds. If a web page changes, then this book is updated with new information.
Sometimes it can take a while for new pages or changes that the spider finds to be added to the index. Thus, a web page may have been “spidered” but not yet “indexed.” Until it is indexed — added to the index — it is not available to those searching with the search engine.
Search engine software is the third part of a search engine. This is the program that sifts through the millions of pages recorded in the index to find matches to a search and rank them in order of what it believes is most relevant. You can learn more about how search engine software ranks web pages on the aptly-named How Search Engines Rank Web Pages page.
Major Search Engines: The Same, But Different
All crawler-based search engines have the basic parts described above, but there are differences in how these parts are tuned. That is why the same search on different search engines often produces different results. Some of the significant differences between the major crawler-based search engines are summarized on the Search Engine Features Page.
How Search Engines Rank Web Pages
its too big to post so check the link..
searchenginewatch.com/showPage.html?page=2167961
ok now i think its enough on intro part.. now posting links to refer..
Nice animated explaining How SEARCH ENGINE works..
http://www.learnthenet.com/ENGLISH/animate/search.html
Read what wikipidea says about SEARCH ENGINE and WEB SEARCH ENGINE..
http://en.wikipedia.org/wiki/Search_engine_%28computing%29
http://en.wikipedia.org/wiki/Web_search_engine
A very well posted difference between Google, Yahoo and Ask.. also explaining major technical related stuff associated with SEARCH ENGINE..
also look for Recommended things in the site while making or using a SEARCH ENGINE..
http://www.lib.berkeley.edu/TeachingLib/Guides/Internet/SearchEngines.html
A very detailed tutorial.. and specifically abt SPIDERS
http://www.webreference.com/content/search/how.html
http://www.monash.com/spidap4.html
A step by step understanding
1. Introduction to How Internet Search Engines Work
2. Looking at the Web
3. Building the Index
4. Building a Search
5. Future Search
6. Lots More Information
7. See all Internet Basics articles
http://computer.howstuffworks.com/search-engine.htm
That’s all.. I hope all of u can understand SEARCH option in better way now.. use it
The Search Engines ability to find corrections is with the help of a function called “levenshtein”.
The function can take two strings as parameter and calculates just the number of insert, replace and delete operations needed to transform one string to another.
soundex and metaphone are two other similar functions.
http://in.php.net/manual/en/function.levenshtein.php
What is SQL Injection?

it is very popular hacking tool
What is SQL Injection?"An attack technique used to exploit web sites by altering backend SQL statements through manipulating application input.
"SQL Injection happens when a developer accepts user input that is directly placed into a SQL Statement and doesn't properly filter out dangerous characters. This can allow an attacker to not only steal data from your database, but also modify and delete it. Certain SQL Servers such as Microsoft SQL Server contain Stored and Extended Procedures (database server functions). If an attacker can obtain access to these Procedures it may be possible to compromise the entire machine. Attackers commonly insert single qoutes into a URL's query string, or into a forms input field to test for SQL Injection. If an attacker receives an error message like the one below there is a good chance that the application is vulnerable to SQL Injection.
Microsoft OLE DB Provider for ODBC Drivers error '80040e14'[Microsoft][ODBC SQL Server Driver][SQL Server]Incorrect syntax near thekeyword 'or'./wasc.asp, line 69
watch movies without money
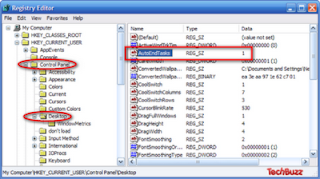
Speed Up Windows XP Shutdown
which automatically kills non-responding apps instantly without interrupting the shutdown process. Before attempting this hack, please have a backup of your registry, just in-case something gets screwed up.
2.Expand the Registry Editor Tree and find HKEY_CURRENT_USER\Control Panel\Desktop
3.Edit AutoEndTasks Key from the right pane and assign to value to 1 (by default the value is 0)
online video sharing site
download any format video online

create gif image online

Unlock yahoo Account When its locked

Some useful Softwares for your pc
single download

How to use it :
1) Just visit File2HD and enter the URL from which you want to download any file.
2) Now, select the option that suits your need. If you want to download images just select the image radio button .
3) Do not forget to put a tick on I have read and agree to the Terms of Service.
4) When you will click on Get Files, it will show you all the list of images present on that web page and you can download images simply by right clicking on the link and selecting Save Target As
download creative photo effects software

Creative is a simple tool that lets you apply very original effects to your photos
, in such a way that they look like outlined sketches. The effect not only achieves an eye-catching result, but also turns bitmap images into scalable drawings that can be easily printed in large sizes to use on posters, t-shirts and the like.
All you have to do is open up any image in Creative and the effect will be applied immediately. You can then use the built-in sliders to adjust the settings and fine-tune the result. Creative also lets you easily colorize the image, and includes a wide color palette for that aim. Finished graphics can be saved in a variety of formats: PDF, GIF, PNG and even SVG.
Creative is easy to use and produces attractive results, but the program still has room to improve, especially in usability. There's no option to undo changes and images are hard to manage within the interface.
Download Here
Top 10 Tips To Improve System Speed (Windows XP)
 1.Let your PC boot up completely before opening any applications.
1.Let your PC boot up completely before opening any applications.2.Refresh the desktop after closing any application. This will remove any unused files from the RAM.
3.Do not set very large file size images as your wallpaper. Do not keep a wallpaper at all if your PC is low on RAM (less than 64 MB).
4.Do not clutter your Desktop with a lot of shortcuts. Each shortcut on the desktop uses up to 500 bytes of RAM
5.Empty the recycle bin regularly. The files are not really deleted from your hard drive until you empty the recycle bin.
6.Delete the temporary internet files regularly.
7.Defragment your hard drive once every two months. This will free up a lot of space on your hard drive and rearrange the files so that your applications run faster.
8.Always make two partitions in your hard drive. Install all large Softwares (like PSP, Photoshop, 3DS Max etc) in the second partition. Windows uses all the available empty space in C drive as virtual memory when your Computer RAM is full. Keep the C Drive as empty as possible.
9.When installing new Softwares disable the option of having a tray icon. The tray icons use up available RAM, and also slow down the booting of your PC. Also disable the option of starting the application automatically when the PC boots. You can disable these options later on also from the Tools or preferences menu in your application.
10. Protect your PC from dust. Dust causes the CPU cooling fan to jam and slow down thereby gradually heating your CPU and affecting the processing speed. Use compressed air to blow out any dust from the CPU. Never use vacuum.
Recover deleted files for free
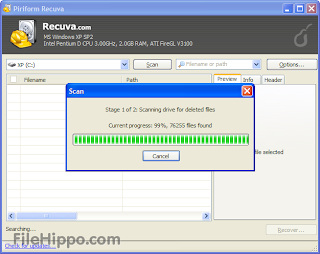
You might have fallen in a situation where you have accidentally deleted any file/folder from your computer and wanted to recover it back. Here is a freeware forwindows called Recuva Data Recovery software to restore files that have been accidentally deleted from your computer.This includes files emptied from the Recycle bin as well as images and other files that have been deleted by user error from digital camera memory cards or MP3 players. It will even bring back files that have been deleted from your iPod, or by bugs, crashes and viruses.
Download
Hot to Fix Taskbar/Toolbar Problems

* Taskbar context menu is disabled. No menu appears when you right-click on taskbar.
* "Lock the Taskbar" option is disabled.
* Can't add toolbars using "Toolbars" option in Taskbar context menu.
* Can't open Taskbar Properties. An error message appears.
* Can't resize or move Taskbar.
=======================================
1. Taskbar context menu is disabled. No menu appears when you right-click on taskbar.
Sol. Open regedit and goto:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
In right-side pane, delete "NoTrayContextMenu" DWORD value.
=======================================
2. "Lock the Taskbar" option is disabled. Whenever you right-click on Taskbar, "Lock the Taskbar" option is grayed out:

HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
In right-side pane, delete "LockTaskbar" DWORD value.
3. Can't add toolbars using "Toolbars" menu in Taskbar context menu. All options are grayed out:

Open regedit and goto:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
In right-side pane, delete "NoCloseDragDropBands" DWORD value.
=======================================
4.Can't open Taskbar Properties.
Whenever you click on "Properties" in taskbar context menu, an error message appears:
Open regedit and goto:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
In right-side pane, delete "NoSetTaskbar" DWORD value.
=======================================
5. Can't resize or move Taskbar even "Lock the Taskbar" option is unchecked.
Open regedit and goto:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
In right-side pane, delete "TaskbarSizeMove" DWORD value.
Phishing -Get Yourself Protected From Being Phished

It is a two part procedure:
1) A site is hacked and a 'phishing' page set up...it is supposed to look identical to a Bank, or PayPal, or a credit card institution's main page.
2) Another site (typically on another server) is again exploited, this time for spamming purposes.
The spam will typically direct you to the phishing page, where the victims type in their information, and are kicked out.
From there it's a matter of cleaning out bank accounts and getting the money where it can't be taken back.
The hard part is there are dozens of phishing central sites and the phishing/spamming sites are blocked or filtered when users report such links found phishing.
A phishing link will usually try to direct you to a fraudulent website that mimics the appearance of a popular website or company. The spoof website will request your personal information, such as credit card number, Social Security number, or account password.
You think you are giving information to a trusted company when, in fact, you are supplying it to an online criminal.
Deceptive URLs.
Be cautious. Some fraudsters will insert a fake browser address bar over the real one, making it appear that you’re on a legitimate website .
Restart your crashed Applicaton instantly

Application Monitor is a program that constantly checks the processes previously chosen by the user, and when it detects that one of those processes has stopped working it will start it again.
With Application Monitor you will always be sure that your important processes are running.
AppMonitor has been developed keeping in mind all those admin and power users who use programs that must always been running (such as webserver, database, mailserver, p2p) and that don't have a built-in restart function.
With Application Monitor you will always be sure that your important processes are running. AppMonitor has been developed keeping in mind all those admin and power users who use programs that must always been running (such as webserver, database, mailserver, p2p) and that don't have a built-in restart function.
System Requirements :
Operating System :
Windows 98 - ME - NT 4(service pack5) - 2000 - WindowsXP
Libraries : You must have installed the Microsoft .NET Framework 1.1 or higher, freely available on Microsoft site.
Click here to visit the download link from the website.
Hide Files in Image Files

Crack MMC Password

Sometimes you forgot the password for your own memory card/sd card especially if you have a lot of electronic device such as handphone, digital camera etc and you are some kind of persons who don't want anyone access your private collections in your phone memory card. Here is one of simple steps to crack memory card.Follow the Steps1. Install the File explorer Software e.g. SELQ of Fileman thru data Cable or Bluetooth in Phone memory2. Then Insert The Blocked MMC3. Open the File Explorer Software4. goto C:\ i.e Phone Memory5. goto System6. Goto Find and Search MMcstore7. Send this file by Bluetooth or Infraread to your PC8. Rename the file MMCSTORE to MMCSTORE.TXT9. pen the file and the password off the MMC will be there...
Print your documents Anywhere

Have you ever wanted that you want to print your docx on your friend pc or some where else.here is the solution called PrinterAnywherewith which you can print documents and photos on other people’s printers as easily as on the local one connected to your machine. It is user friendly application and very easy to use.Something about this software is* Share your printer with anyone you want* Print from any application* No need to send emails with attachments* Fast and secure* Easy installation* FREE!download from here
Fast defragmention through UltraDefrag
The console is another option for those that prefer the command line. It is also allows you to run UltraDefrag from the task scheduler and scripts. Finally, the native executable will run at boot time in a manner similar to chkdsk.
The design of UltraDefrag is very simple. There are no skins and other unnecessary stuff. It is a small and powerful program!download from here
Online tv player
 Online TV Player lets you watch 850+ Internet TV and listen to 1500+ online radio stations. It allows you to watch TV directly without going to Web sites. It supports both Windows Media and Real Video, and can set the screen window to any size you want.donload from here.
Online TV Player lets you watch 850+ Internet TV and listen to 1500+ online radio stations. It allows you to watch TV directly without going to Web sites. It supports both Windows Media and Real Video, and can set the screen window to any size you want.donload from here.Share your desktop with very easy way

There are many applications out there that allow you to share desktops but perhaps none that do it more easily and simply than Crossloop.CrossLoop is basically a free secure screen sharing utility designed for people of all technical backgrounds so you don’t need to be a geek to use it. It allows you to connect to another user's computer and share their desktop without having to change any firewall or router settings. This is obviously perfect if you need to find out why someone is having problems with their PC or if you just want to simply share information with them.The key to this program’s appeal is its simplicity. In fact, the developers claim you’ll be sharing desktops within 60 seconds of installation. After installing CrossLoop, you will see a welcome screen with two tabs. Select the ‘Join’ tab if you would like to connect and control a friend's PC. Select the ‘Host’ tab if you would like to temporarily share access to your PC.
play with your photos with photo bunny


 Want to make your friends look silly, for a laugh? Photo-Bonny is the perfect tool for the job!This simple photo editor helps you create hilarious photo compositions by combining your own images with a bunch of small, nicely designed clipart graphics. The collection includes various items such as wigs, glasses, objects, symbols and all sorts of elements to 'decorate' the selected photo. Photo-Bonny also features a wide selection of ready-made frames with different designs for all occasions.Using Photo-Bonny is really easy. All you have to do is open the photo you want to work with and start adding as many clipart items as you want. They can be placed anywhere on the image and can be freely resized. Photo-Bonny also includes a brush tool to paint the photo, and a basic photo viewer.Photo-Bonny is definitely a great tool for easy, fun photo compositions, though the clipart collection is a bit limited and cannot be expanded.download from here
Want to make your friends look silly, for a laugh? Photo-Bonny is the perfect tool for the job!This simple photo editor helps you create hilarious photo compositions by combining your own images with a bunch of small, nicely designed clipart graphics. The collection includes various items such as wigs, glasses, objects, symbols and all sorts of elements to 'decorate' the selected photo. Photo-Bonny also features a wide selection of ready-made frames with different designs for all occasions.Using Photo-Bonny is really easy. All you have to do is open the photo you want to work with and start adding as many clipart items as you want. They can be placed anywhere on the image and can be freely resized. Photo-Bonny also includes a brush tool to paint the photo, and a basic photo viewer.Photo-Bonny is definitely a great tool for easy, fun photo compositions, though the clipart collection is a bit limited and cannot be expanded.download from hereLogin with Multiple ID at the Same Time

This trick works when you want to login with multiple ID of orkut, gmail or yahoo.
Step 1:
Open system properties(by right clicking my computer), choose tab advanced, click to environment variables button. in system variables section, click new. type this information to each textbox.
variable name: moz_no_remote(should be all small letter)
variable value: 1
press ok to close all windows.
Step 2:
Open firefox icon's properties(from desktop and quick launch). add extension -p to command line(like "c:\program files\mozilla firefox\firefox.exe" -p). press ok.
While starting firefox u have to create two separate profiles of firefox so that u can login to two accounts of any(orkut,yahoo,rediff or anything else).......for three logins create three profiles of firefox.........
How to: Disable/Enable the Windows XP Welcome Screen
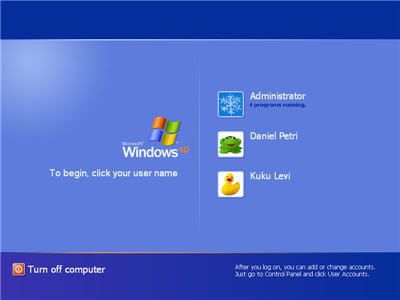
Windows XP gives the user a couple ways to log into the computer. You can use the traditional or classic method of typing in the username and password to login or you can use what's called the Welcome Screen to login.
What if you want to change the way your computer logs in, can you disable or enable this Welcome Screen?
The Windows XP Welcome Screen is tied to another feature called "Fast User Switching".This feature lets a user leave all his programs running if another user needs to use the computer.
The first user can Log Off the session and Switch User back to the Welcome Screen so that another person can use the computer.
When the second person is done, the user can switch back to his profile with all the programs still running where they left off.
In order to use this feature, you have to use the Welcome Screen.
However, if you dont need or want this feature, follow the instructions below to remove the Welcome Screen.To do this follow the directions below:Remove the Welcome Screen
If you dont want to use "Fast User Switching", you may want to disable the Welcome Screen.You must be logged in as an Administrator to do this.To do this follow the directions below:
1) Click on Start
2) Click on Control Panel
3) Double-click on User Accounts
4) Click on "Change the way users log on or off"
5) Uncheck "Use the Welcome Screen"(Note: this will also disable "Fast User Switching")
6) Click on Apply Options
7) Close the User Accounts window and the Control Panel
8) The next time you reboot your computer, the classic login prompt will be used
What if I dont want the Welcome Screen OR the classic prompt?
Can I disable both?To Login automatically to a user account, follow the instructions below:
1) Click on Run
2) Type in the following command
control userpasswords2
and click OK
3) Highlight the user you want to log into automatically, then uncheck the box for"Users must enter a username and password to use this computer"4) Click on Apply and you'll be asked to verify the username and password to log in automatically5) Click OK and the next time you restart your computer, you'll automatically be logged in without having the classic prompt or Welcome Screen.Is there a utility I can use to accomplish this?You can download a utility for Windows XP called TweakUI that will allow you to change the way you log into Windows XP, along with allowing you to change alot of other features.You can download TweakUI for Windows XP from the Microsoft Powertoys web page at:
http://www.microsoft.com/windowsxp/downloa...ppowertoys.mspx
AutoPager FASTER WEB BROWSING

AutoPager is a Firefox extension which automatically loads the next page of a site inline when you reach the end of the current page for infinite scrolling of content. By default AutoPager works with a ton of sites, including Lifehacker, the New York Times, Digg, eBay, Amazon, Yahoo, YouTube, flickr, live, msn, myspace, wikipedia, ebay,taobao,Twitter and, of course, Google. AutoPager is a free software. AutoPager is also an open source software.
You can Install AutoPagerInstall AutoPager Now. Or download the latest version of the AutoPager from addons.mozilla.org.
Forever delete your files with Freeraser 1.0

Deleting a file in Windows doesn't mean that it disappears forever. The system simply marks the space as free again, but the actual file is still there and can easily be recovered with the appropriate software.So if you want to make sure your deleted files can't be recovered later on, use Freeraser, an alternative Recycle Bin for Windows that erases files securely so that they can't be retrieved with a recovery tool. The program features a nicely-designed resizable icon with transparency effects, which looks much better than the standard Windows bin.Freeraser supports three deletion methods (fast, forced and ultimate) and works really efficiently. Just bear in mind that you need to be sure you want to delete those files: although the program lets you stop the deleting process, it doesn't have an "undo" option. Also, it would be great to have it included in Windows context menu, just like the Windows Recycle bin is.
download from here
Self distructing Email
 Every time that you send an email, copies are stored permanently on multiple email
Every time that you send an email, copies are stored permanently on multiple emailservers as well as the recipient's inbox and anyone they decide to send it to. Your emails can be stored and scanned in more places than you can imagine. Do you want people storing your email messages forever? Do you want something that you type today to be used against you tomorrow, next week, next month or even in the next decade?
Until now, everyone else has had control of the email that you have sent. BigString gives you back control of your email, acting like an automatic shredder for your email. You can self-destruct or change an email that's already been sent or read. Don't leave your messages sitting in peoples' inboxes forever. Get a free BigString email account to protect your privacy.
BigString takes the risk out of email
Now, with BigString, you can finally take the risk out of email and put an end to "sender regret." It is the world's first & only email service that thoroughly protects your safety and privacy.
BigString's exclusive, patent-pending technology enables you to prevent your personal or business information from lingering indefinitely in someone else's inbox. It also restricts private pictures or messages from being indiscriminately spread throughout cyberspace! Now your sensitive photos can't be posted to unseemly web sites or printed for circulation amongst total strangers.
BigString lets you have second thoughts
BigString shifts the control from the recipient to YOU the sender. BigString grants the luxury of second thoughts, the power to limit message viewings, and the choice to delay email transmission.
You can reword a message fired off in anger or haste or completely delete it! You can recall a botched résumé for revision or erase a tasteless joke. You can make a work of art or photograph print-proof. You can prevent a love letter from being forwarded. You can set an expiration date on an emailed price quote or business offer or you can simply pull back an email to eliminate typos.
BigString takes the danger out of clicking
BigString guarantees that clicking "send" will never again be an irreversible disaster. Now YOU decide the fate of your emails. You decide where they end up, who sees them and for how long. BigString emails can be destroyed, recalled or changed even after they've been opened! The freedom is yours, the options are yours, and you're the boss with BigString.
BigString is easy to use
BigString is as easy to use as any other email and there's nothing to download! Don't be resigned to the mercy of your recipient. You don't want your every action to be carved in stone because sometimes you just NEED to take it back!
Here are just a few of the many applications of BigString
Erasable, Recallable, Non-Printable Email.
Executives: Protect your business and safeguard your email. Now you never have to worry about sending the wrong attachment or completely forgetting it. Misspelled words, incorrect dates, or other typos can all be fixed even after your message has been sent. You can even "pull an email back" to delete expired price quotes, old business offers or dated legal material. BigString is your email insurance.
On-Line Daters: You don't want your personal information like pictures, phone numbers or intimate notes, circulated around the Internet! BigString prevents your pictures and messages from being printed or forwarded. You can set an expiration date for an email or self-destruct it at will. You can choose the number of times you'll allow a picture to be viewed before it disappears. BigString protects your privacy!
Artists and Photographers: Now with BigString you can confidently email proofs and samples without the slightest fear that they will be printed or saved for later use without your authorization. Use BigString to make your image non-savable and non-printable! Limit the number of times a client can view a piece before you have it self-destruct. You can even recall a sent email to delete an old price quote or alter a new one. You can also prevent it from being forwarded to other customers. BigString protects your rights of ownership!
Copywriters: Spelling or punctuation errors that can cost time, money, or embarrassment are now a thing of the past. With BigString, clicking "send" is no longer an action "carved in stone." Accidentally arranging paragraphs in the wrong order will no longer mean a lost account. With the technology of BigString you can recall that mistake-ridden copy and correct the errors even after your email has left the outbox. You can self-destruct what you sent all together and replace it with a fully revised version. Only you will know this switch has occurred! With BigString you can confidently send non-printable, non-savable sample copy. You no longer have to worry that it will be used without your knowledge. You're the boss with BigString.
All the features of Regular Email plus:
Self-Destructing Email
Recallable/Erasable Email
Non-Forwardable Email
Non-Printable/Savable Email
Advanced Email Tracking
Masquerading
All the storage you need
Secure Email
Video Email
Large Attachment Capacity
Automatic Message Highlighting
Advanced Spam and Virus Filtering
Advanced Message Sorting
Fun Email Effects
Create Thousands(1000) of Fake Orkut Id/Login

Now once you have installed Mozilla and
Greasemonkey then you have to install one script from Here.When you open this link you will find one button at right “Install Script” So click on this when you click on this it will ask to install this script, If you want to install this script then click on “Install Script”. It will install script in 2 to 3 seconds. Now you are ready to make thousand of fake profiles in Orkut and by this you can also increase members of your community in easy way.
Now to start fake login id in orkut just go to sign up page (or go to www.orkut.com and then click on join now). When you open sign up page then you have prompted by one box asking you to number of fake id you want to create. just enter number of fake if you want to create then it will automatically enter all information, But you have to enter numbers shown in image verification. Enter number shown in image verification then clcik on “I Accept, Create my account” button it will create your fake id, Now logout from this id, So it again fill form for you automatically and you have to enter only image number in text box. This type you can make fake id in Orkut and increase your community members.If you have any problem in this then you can post it in your comment.










